What would you do if a suspicious stranger came up to you on the street and tried to lure you down a dark alley? You’d probably sense danger and either walk away quickly or call for help.
But what if the stranger approached you through email? You might feel it’s safe to click on a link in the email or open an attached file—but it’s often a trap.
Every day, cyber criminals use malicious emails to try to scam individuals and organizations — a type of attack known as “phishing.” Interacting with a phishing email carries serious risks for you, the University, and even your family and friends. Fortunately, we can all learn strategies for recognizing and avoiding these attacks.
What is phishing?
In a phishing attack, cyber criminals use deceptive emails to “fish for” information and lure people into falling for their scam, often by posing as a trustworthy entity or person (for example: University senior management, IT personnel, popular social web sites, banks, and credit card provides.) These emails are carefully designed to trick you into revealing financial information, login credentials, or other sensitive information. Or they may secretly install malicious software (malware) that compromises your device and the files on it.
Phishing emails typically pressure you to act quickly, without thinking. They play upon strong emotions — such as curiosity, fear, or greed. These psychological manipulation tactics are sometimes known as “social engineering.”
Phishing emails also use a variety of technical tricks to steal information:
- Malicious web links – You’re asked to click on a link that takes you to an imposter website or to a site infected with malware.
- Malicious attachments – You’re urged to open an unexpected attachment that contains malware.
- Fraudulent data-entry forms – You’re prompted to fill in sensitive information like user IDs, passwords, credit card data, and phone numbers.
Is phishing really my problem?
Many companies have suffered serious data breaches that exposed everything from business secrets to the confidential data of millions of people. These data breaches often start by tricking one person with a phishing email, giving criminals a foot in the door.
Phishing can affect your personal life, too. Whether at home or here at the University, falling for a phishing email can have serious, long-term consequences.
At the University:
- Loss of University funds
- Exposed personal information of students and coworkers
- Outsiders accessing confidential communications, files, and systems
- Files becoming locked and inaccessible
- Damage to the University’s reputation
In your personal life:
- Money stolen from your bank account
- Fraudulent charges on credit cards
- Tax returns filed in your name
- Loans and mortgages opened in your name
- Lost access to photos, videos, and files
- Fake social media posts made to your accounts
What can I do?
While the University has several controls to reduce the impacts of these attacks, attacks can still happen due to human error. Therefore, to best mitigate or avoid these attacks, we all must be vigilant and diligent in identifying these red flags, verifying the request is legitimate, and periodically reviewing training to keep our detection skills sharp.
Here are three things you can do?
1. Look out for red flags
Below are some specific red flags that you can look out for when you receive a suspicious request or message:
- Unexpected and/or vague requests: Ignore any unexpected or vague requests, such as unclear SharePoint or OneDrive file-sharing requests or requests to hastily circumvent policy or procedure.
- Misspellings and/or poor grammar: Often you will find misspellings and/or poor grammar within social engineering attacks, especially if the message appears to be from someone you know, and the language used is much different than to what you are accustomed.
- Scare tactics: These attacks depend on scaring you, such as with a lawsuit, that your computer is full of viruses, your account may be locked, suspended, or deleted, that your personal information may be divulged, or that you might miss out on a deal that is too good to be true. Do not react to scare tactics!
- Urgency: Review the words or phrases that indicate a deadline or a need to take quick action (i.e., individual needs to get into the building because of a late meeting). Some of these words or phrases could include "final notice," "urgent," "action required," "your account will be deleted,” or “your account will be locked.”
- Misleading hyperlinks: Always review web addresses (URLs) in hyperlinks. Hover over hyperlinks and ensure the URL relates to the location you are expecting to go. Malicious websites may look identical to a legitimate site, but the URL may use a variation in spelling or a different domain (e.g., .com versus .net). If the website looks different than when you last visited, be suspicious and do not enter any personal or financial information unless you can verify that the site is secure.
- Deceiving sender email addresses: Malicious individuals use misspelled email addresses, obfuscated email addresses (e.g., testperson.neomed.edu@gmail.com instead of testperson@neomed.edu), spoofed email addresses (i.e., appears to be an email from a neomed.edu account however does not actually exist), or compromised email accounts (i.e. someone who had their credentials compromised and now a malicious user is attempting to phish others) to mislead the recipient.
- Browser warnings: Be aware of any warnings that your web browser may display (i.e., warning screens, dangerous labels next to the web address.)
Here is an example of a real phishing attack the University received and the red flags associated with it:
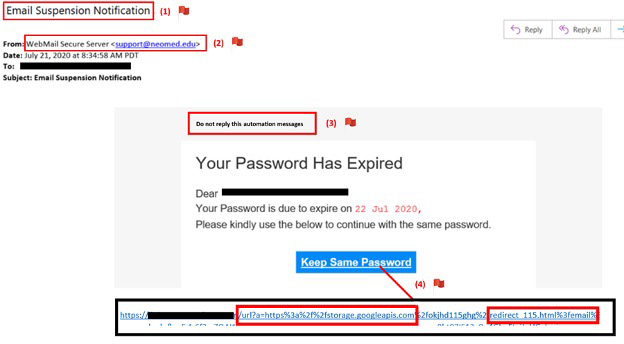
Red Flag 1: Scare tactics – The email subject indicates that the individual’s email account will be suspended, encouraging the individual to open the email to review the content.
Red Flag 2: Deceiving Sender email addresses – It appears that this is coming from a legitimate neomed.edu email address, however this attempt is making it appear real (spoofing). Additionally, University IT emails do not come from this address.
Red Flag 3: Misspellings and/or poor grammar – This portion of the message includes poor grammar, such as missing words and incorrect verb/subject agreement.
Red Flag 4: Misleading hyperlinks – Upon hovering over the hyperlink, the web address listed is taking the user to “storage.googleapis.com” (expected to go to a Microsoft page) and includes a “redirect” command. This is an attempt to redirect someone to a malicious site.
2. Verify that the request is legitimate
If you are ever unsure whether if a request or message is legitimate at the University, contact the NEOMED Help Desk (help@neomed.edu or 330-325-6911). You can also take steps when you identify phishing red flags to determine if the request is legitimate or not:
- Verify any suspicious requests by contacting the individual/entity independently. Legitimate companies and organizations will give you a real business address and a way for you to contact them back, which you can independently verify on a company website, support line, etc. Do not trust people who contact you unexpectedly claiming to represent the University. If you receive an email or phone call requesting you call them and you suspect it might be a fraudulent request, look up the organization’s customer service number and call that number rather than the number provided in the solicitation email, phone call, or text message. If you are unsure whether an email request is legitimate, contact the organization using information provided on an account statement or other source, not the information provided in the potentially fraudulent email.
- The President of the University emails you unexpectedly to purchase gift cards. Instead of doing so, you should notify the NEOMED Help Desk and call the President’s Office to verify its legitimacy.
- You receive a call from what you believe to be your credit card company stating that your account has odd activity on it and you need to provide your credit card details over the phone to verify they are talking to the correct person. Instead of doing so, you should request their name and phone number and indicate you will call them back. After hanging up, you should call the number printed on the back of your credit card and speak to a different representative confirming that odd activity is legitimate.
- Review an email header’s sender email address: An email header is a log of an email’s technical details that both the sender and recipient can see, including any email addresses that are involved in the conversation, the servers the email passed through while being sent, and more. By reviewing email headers, you can compare the email address presented in your email to the sender address in the email header. If they do not match and you see an irregular or odd email address within the email header, it is likely fraudulent.
- See this brief Microsoft how-to article: View Email Headers in Outlook
3. Training to keep your skills sharp
The University also has developed training on phishing, which can be found within the NEOMED Success Center: NEOMED Information Security Awareness Training Course: Phishing
Additionally, here are some short videos (2-4 minutes) and tips that provide more information and tips on phishing and social engineering:
- SANS Security Awareness: Social Engineering
- SANS Security Awareness: Email and Phishing
- Centre for the Protection of National Infrastructure (CPNI): Phishing and Spear Phishing
- U.S. Cybersecurity and Infrastructure Security Agency: Security Tip – Using Caution with Email Attachments
- U.S. Cybersecurity and Infrastructure Security Agency: Security Tip – Avoiding Social Engineering and Phishing Attacks
What should I do if I fall for a phish?
The best and most critical thing you can do is notify the appropriate parties if you happen to fall victim to a phishing attack.
For University accounts, data or systems:
- Notify the NEOMED Help Desk immediately (ext. 6911 or help@neomed.edu). A timely notification can significantly minimize further impact!
For personal accounts or information:
- Watch for any unauthorized charges to your account(s). If you believe your personal financial accounts may be compromised, contact your financial institution immediately to get guidance on freezing or closing the account(s). Additionally, you can flag your credit reports by contacting the fraud departments of any one of the three major credit bureaus: Equifax (800.685.1111); TransUnion (888.909.8872); or Experian (888.397.3742).
- Consider reporting personal attacks to your local police department and filing a report with the Federal Trade Commission or the Internet Crime Complaint Center. Make sure you keep a copy of the police report in a safe place.
Submitted by Jonathan Wagner, information security, training & compliance manager, Department of Information Technology
